Context-Aware
Advertising Systems for Mobile Devices
James Wooltorton
Abstract
Mobile devices, such as PDAs and mobile phones, present excellent
opportunities for directly targeting advertising at end-users. By utilising context through context-aware
system it should be possible to produce highly personalised advertising and
avoid bombarding users with large amounts of unsuitable, badly matched data.
This paper will discuss the areas associated with the development
of a context-aware system for pushing product advertisements to mobile devices
using contextual information to determine the most appropriate product from a
retailer’s catalogue. This review will discuss ubiquitous computing,
context-awareness, contextual data, location awareness, mobile advertising
systems, as well as looking at possible approaches and reviewing some existing
applications.
Introduction
Mobile devices are by their very nature private and personal
devices. How many of us have received a text message only to be disappointed by
annoying service messages or unsolicited advertising? Context-aware systems present excellent opportunities for
directing highly targetable advertisements at end-users through these devices. This can be achieved by utilising
contextual information from these devices and by learning end-user preferences
and habits. Although, it is critical
for the acceptance of any such system that is does not feel intrusive, whilst
also putting considerations for security and privacy foremost. To address these problems this paper focuses
on the major challenges associated with developing context-aware systems for
mobile advertising.
We live in a digital age, surrounded by low-cost,
ever-increasingly powerful computing devices, which are becoming progressively
more integrated into our everyday lives.
These embedded devices are already in our cars, homes, workplaces,
refrigerators, and with the current technological trends it seems inevitable
that they will commonly become both wireless and mobile. Such a scenario of large numbers of embedded
and mobile devices, all invisibly communicating over an interconnected network,
is an ideal environment for ubiquitous computing.
Ubiquitous computing
Ubiquitous computing names the third wave in computing (figure 1),
just now beginning. First were mainframes, each shared by lots of people. Now
we are in the personal computing era, person and machine staring uneasily at
each other across the desktop. Next
comes ubiquitous computing, or the age of calm technology, when technology
recedes into the background of our lives.(Weiser, 1994)
Wesier first introduced ubiquitous computing as “the method of
enhancing computer use by making many computers available throughout the
physical environment, but making them effectively invisible to the user”
(Weiser, 1993). Abowd et al
extended this idea by saying “ubiquitous computing is the attempt to break away
from the traditional desktop interaction paradigm and move computational power
into the network and environment that surrounds the user”. (Abowd et al., 1998). Both Wesier and Abowd saw the potential in
this radical new approach to computing, heralding the idea of harnessing the
power of these devices, invisibly integrating them in order to enhance our
modern lives. Weiser, perfectly sums it
up by saying “It is invisible, everywhere, computing that does not live on a
personal device of any sort, but is in the woodwork everywhere” (Weiser, 1994)
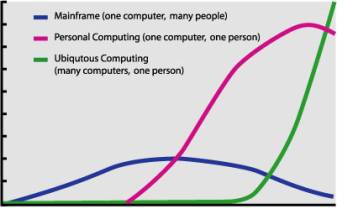
Figure
1: The Three Ages of Computing (Weiser, 1996)
There
are many challenges which face developing truly ubiquitous systems, it will
require “much new work in operating systems, user interfaces, networks,
wireless, displays and many other related areas.” (Weiser, 1994) Central to ubiquitous computing are the key
concepts of concurrency and parallelism, so from a developmental point of view
existing methodologies are not suitable for ubiquitous systems, a view backed
up by Borah, who highlights that “existing middleware for client server
computing such as .NET, J2EE and CoBrA were not designed for ubiquitous
computing”. (Borah, 2005) A
developmental platform is required where these concepts are intrinsic and not
bolted on to an existing solution.
Ubiquitous Environments
One
such approach is the Indus platform (Borah, 2005), first conceptualised back in
2002, it is an attempt to embrace object-orientation principles and extend them
to ubiquitous systems. Indus is a
software agent platform, designed specifically for ubiquitous computing, it
comprises of a programming language, libraries and containers or run time
environments for cross platform distribution.
Indus targets specific ubiquitous application groups; these include
Intelligent Transport Systems, Supply Chain Management, Personal Area Networking
and Control & Automation.
The
Indus programming language extends the Java platform (Java API, 2002),
introducing new concepts for context, and ports, as well as replacing the Java
Interface type with two new interface types called Agent and Component,
therefore every Indus class is either an Agent or a Component.
·
An agent in Indus represents a role, additionally an agent
can have several methods. Each method
represents a task that can be implemented by an actor representing that role.
·
Components are re-usable program building blocks, that
implement static functionality of a system and compose other components.
In
Indus, we can model any system as a set of concurrently executing agents. The Indus libraries include general purpose
services for self configuration, service discovery, security, intelligent
routing, transaction and policy management. Additionally, Indus compiles directly to native code on a number
of systems, making it highly deployable.
On enterprise platforms Indus compiles to Java byte code and runs using
the JVM, whilst on mobile platforms it compiles directly to C code and binary
executables.
Context
and Context Awareness
Context
”The use of context is increasingly important in the fields of
mobile and ubiquitous computing, where the user’s context is rapidly changing.”
(Abowd et al., 1999)So what exactly is context? We can think of context
as the circumstances under which a device is being used, and its situational
information during events, or as summarised by Abowd et al, “ any
information that can be used to characterise the situation of an entity, where
an entity can be a person, place or physical or computational object.” (Abowd
& Dey, 2002)
Korkea-aho provides some useful examples (Korkea-aho, 2000) of
contextual data that can be utilised in a context-aware system, these include:
·
spatial information - e.g. location, orientation, speed and
acceleration
·
temporal information - e.g. time of day, date, day of week
·
environmental information e.g. temperature, weather conditions
·
activity - e .g. shopping, dining, walking, working.
·
social situations - e.g. people you are with or who is nearby.
·
personal information -
e.g. mood, blood pressure.
Context-Awareness
Abowd and Dey define context-awareness or context-aware computing
as “the use of context to provide task-relevant information and/or services to
a user.” (Abowd & Dey, 2002)
Schilit says “context-aware computing devices react to their changing
environment in an intelligent way so as to enhance the computing environment of
the user.” (Schillit et al, 1994) It is
the goal of any context-aware system to be able to interpret low-level
contextual data and make assumptions about the user’s current situation.
A system can be thought of as context-aware if it can extract,
interpret and use contextual information and adapt its functionality according
to the current context of use (Pascoe 1997).
Abowd et al (2000) and Troung et al (2001) identified the following
questions, known as the five W’s, which any context-aware system needs to
address: Who is using the system? What is he/she doing? Where is he/she
located? When does the interaction take place?
Why is the user doing that specific action?
Pascoe identifies that “the main challenge for any context-aware
system lies in the complexity of capturing, representing and processing this
contextual data.” (Pascoe, 1997) Although this looks at context-aware systems
primarily from a technical stance, a view supported by (Kaasinen, 2002). In fact many context-aware projects cite
more human factors, like privacy concerns (Hong 2004)(Kourouthanasis,
2002)(Newman et al., 1991) or simply the rejection of a system that
feels intrusive (Want et al., 1995), as the key concerns for the success
of a CA system.
Range Values
Another issue often associated with contextual data is dealing
with range values, this is primarily because “context-aware queries rarely
revolve around exact values” (Picco et al., 2005). Picco et al go further to identify
that in context-aware systems queries are often “formulated over value ranges,
and there is a need to deal with imprecise information coming from many
sources”. For example, a system could
represent an individual as aged 18 to 30 instead of their exact ages. Conventional programming languages only
provide facilities for exact matching, a more adaptive approach is required in
order to support data aggregation.
LighTS (Picco et al., 2005), is a lightweight Java API,
which uses a tuple space model inspired by Linda (Gelernter, 1985), to
provide a solution to this problem for context-aware applications. It provides emphasis on supporting range
values and uncertainty in context-aware applications, by providing methods for
specifying upper and lower bounds of range values for matching and using fuzzy
logic techniques for dealing with uncertainty in data.
Context-Aware
Applications
Context-aware systems offer entirely new opportunities for
application developers and for end-users by gathering context data and adapting
systems behaviour accordingly (Baldauf et al, 2005) Some example of early
context-aware systems included the Active Badge (Want et al., 1992),
Xerox PARCTab (Want et al., 1995) and PEPYS (Newman et al., 1991)
projects, all are examples of office based, mobile, location-aware,
applications.
Active Badge
The Active Badge project stemmed from Olivetti research
laboratories in the early 1990's, it was an automated system for forwarding
calls directly to employees, depending on their current location in the
workplace. Each employee carried
around a small personalised device, (the Active Badge) which using a
transmitted IR-signal uniquely identified the carrier, the system could then
track individual employee movements throughout the day and determine the
closest available phone at any time.
ParcTab
The
Xerox ParcTab centred on small wireless palm-sized hand held computers which
where designed to host an office based application. The system provided a number of applications, not all of them
context aware. Early attempts at
context-aware applications like locating local resources or personnel, and
obtaining room information, where merged with more conventional experiments
with mobile office applications such as e-mail, calendar information or even
weather forecasts.
Context-Aware frameworks
A significant challenge for context-aware systems lies in how we
represent and process contextual data, this difficulty in dealing with low
level data that drives context-based systems is a key factor in the relatively
slow emergence of context-aware applications,
a point emphasised by Pascoe, who stated that there is a “lack of a
supporting infrastructure for capturing and processing context data, so
hampering development of context-aware systems”. (Pascoe, 1997) So how do we represent contextual data?
With conventional development paradigms programmers use rigid
structure and definite processes to control data, contextual data though is
altogether more vague. This inherent
uncertainty in contextual data, compared with a developer’s need to define
static structure and rules, mean that we run the risk of compromising the
contextual data itself by attempting to fit it into conventional developmental
practises. Abowd sums this up by
staying that “without good representations for context, application developers
are left to develop ad-hoc and limited schemes for storing and manipulating key
information” (Abowd, 1999). Therefore
a wholly new novel approach is required for context-aware applications, an
example of some of these frameworks include:
Stick-e Note
The Stick-e note architecture (Brown, 1996) (Pascoe, 1997) is a
flexible, extensible, framework for handling context and related events,
focusing on using context to trigger context related behaviours. Stick-e notes introduces the concept of
attaching objects to contexts, much like Post-It™ notes, the idea
being that when a user enters such a context the object will be invoked. Each of these stick-e note objects is a link
between a context (e.g. a place, person, time) and its content (e.g. information,
action), along with triggering information.
This triggering information defines the conditions under which the
content should be invoked, for example we could attach a “go home message”, if
the time is after 5pm.
Context Toolkit
The Context Toolkit (Dey, 2002) is a framework for a distributed
system composed of context widgets. Context widgets, much like the idea of
objects in object orientated approaches, are software components that provide
functions for accessing contextual information, whilst hiding the complexity of
context sensing. The toolkit
provides services for encapsulation of sensors, access to context data
through a network API, abstraction of context data, sharing of context data
through a distributed infrastructure, storage of context data and privacy
protection
CoBrA
CoBrA
(Context Broker Architecture) (Chen, 2004) is an agent-based architecture which
introduces the notion of intelligent spaces for supporting context-aware
computing. Intelligent spaces are
physical spaces (e.g., kitchens, cars, work office and meeting rooms) that
contain intelligent systems that provide services to end-users. Pivotal to CoBrA is the idea of a context
broker that centrally manages the agents.
Agents can be either applications hosted on mobile devices or services
provided by devices within rooms.
Location
Awareness
The Xerox PARCTab and Active Badge projects are, like the majority
of existing context-aware systems, examples of location-aware applications,
that is they primarily use locational information in determining what services
to provide the user. This is due to the
fact that “the location of a device is an element of context that currently can
be easily measured.” (Kassinen, 2003)
Kassinen also identifies that there is a significant “user need for
location-aware services.” (Kassinen, 2003) Context-aware systems dealing with
locational information are widespread and the demand for them is growing due to
the increasing spread of mobile devices (Baludauf et al, 2005) There are
examples of location-aware systems in application areas such as GPS based
navigation, tourist guidance (Berderson, 1995), supply-chain management
(Kourouthanasis, 2002), and office tracking systems (Want et al., 1992)
(Want et al., 1995).
As discussed earlier, one of the key challenges for a context-aware
system is capturing contextual data (Pascoe, 1997) and for a location-aware
system this involves the physical process of locating the device. There are a number of technologies available
for collecting this positional data, the most significant for mobile devices
include:
GPS
GPS (Global Positioning System) is a
satellite navigation system, which can very precisely determine the position of
a device, almost anywhere on the planet.
The system is accurate to within 20 meters, although it is possible to
greatly increase this precision through error-correction and differential GPS
techniques. GPS devices do not work
indoors or in some urban regions.
Common examples of GPS driven devices technology include car or vehicle
tracking systems, although GPS technology is more commonly integrated into
modern mobile phones and PDAs.
Bluetooth™
Bluetooth™ is an international standard,
which allows for wireless communication between enabled devices over a short
range radio frequency. Bluetooth™ technology
is both low cost and globally available, and is becoming increasingly common in
small devices such as mobile phones and PDAs.
It has a range of between 1 –100 meters, depending on the class of the
device. Detecting Bluetooth™ devices
requires specific hardware, and the location of a device is only available when
the device is within range of the service area. There are also some concerns over privacy, blue jacking and bluesnarfing, respectively
spamming and hacking discoverable devices, are examples of technology specific
problems.
WLAN
WLAN (Wireless Local Area Network) was introduced as a wireless alternative to LAN, a method of networking
devices. Although, originally prohibitively expensive, reducing costs, as well
as the introduction of the IEEE 802.11a and g standards, has meant that many
devices including laptops, printers, and PDAs now come with wireless
capabilities as standard. A significant
problem associated with WLAN is security, although this issue has been somewhat
lessened since the introduction of encryption techniques WEP and WPA, and
router based security measures such as MAC address screening. Like Bluetooth, WLAN requires specific
hardware to locate devices, and the device is only available whilst in service
range.
Mobile Context-Aware
Systems
Mobile computing has been one of the
largest computing related growth industries over the last decade, (Government
Statistics, 2003) UK government statistics estimated that in 2003 73% of the
adult population own or use a mobile phone.
Mobile devices have saturated our everyday lives, placing small,
powerful, programmable, computing devices into our pockets; ideal conditions
for the first stages of ubiquitous computing. It is this integration that drives the need for context-aware
systems specifically designed for mobile environments, which provide programs
and services that react specifically to their current location, time and other
environmental attributes. (Baldauf et al, 2005)
This
highlights a need for context-aware applications for mobile devices, although
existing frameworks are not specialised enough to support large scale mobile
systems properly. Context-aware systems for mobile devices require more
specialised architecture than conventional approaches. Mobile devices are continually moving and
are not permanently connected to a network.
This discontinuity of service has to be taken into account when
designing architecture for mobile devices. (Tandler, 2001) Hofer et al say that
Context-Awareness is especially interesting in mobile devices where the context
of the application is highly dynamic (Hofer et al., 2005) Mobile devices are heterogeneous, so resolution,
memory, computational power and network capacity all vary from device to device
so specific considerations are required. (Hofer et al., 2003)
Hofer
et al went further in identifying a number of requirements necessary for
supporting context-awareness on mobile devices, these being:
- Context-sharing – the
ability to share contextual data with other devices
- Meta information – must
provide information about the conditions under which the contextual data
has been deceived, i.e. the device from the sensor, its preciseness.
- Robustness – the
architecture must be robust enough to handle disconnections from remote
sensors.
- Extensibility – the
architecture should support connections to multiple sensors
- Lightweightness – the
architecture has to take into consideration restrictions of computational
power.
(Hofer et al.,
2003)
Mobile Context-Aware
Frameworks
Hydrogen
The Hydrogen project (Hofer et al., 2002)
is a specialised framework for mobile devices.
Unlike most context-aware systems it relies less on the availability of
a centralised component in distributed systems. Importantly, it distinguishes between remote and local
context. Remote context being
information another system knows about, and local context is information native
to the system. Hydrogen provides
mechanisms for sharing of this contextual data between devices in proximity,
known as context sharing, using peer-to-peer technologies such as Bluetooth or
WLAN.
Mobile Context-Aware
Applications
B-MAD
B-MAD (Bluetooth Mobile Advertising) was
introduced as a “system for delivering permission-based location-aware mobile
advertisements to mobile phones, using Bluetooth™ positioning and
WAP push delivery”. (Aalto et al, 2004)
The system uses a Bluetooth sensor to pro-actively search for nearby
enabled devices. Once located it
obtains the devices unique address and passes this to an Ad Server. The Ad server, a PHP and MySQL platform,
creates an advertisement in either XHTML or WML (Wireless Mark-up Language)
depending on the capabilities of the device.
Using a Push Sender the advertisement is then pushed back to the mobile
device.
Mobile Based Advertising
Consider the following scenario, “Bob is
shopping in a small mall with his Bluetooth enabled mobile phone, invisible to
Bob his phone has been located by the application server and a shopping profile
(containing relevant shopping related contextual data only) has been
exchanged. Using this contextual data
the system quickly matches Bob's details against the retailer’s product
database and attempts to push an advertisement to his mobile device. Bob, a keen walker, receives the
advertisement in the form of a WML message, offering him 10% off a pair of
walking boots in his size.” This is a
somewhat simplistic example, but it does highlight the distinct potential for
context-aware mobile based advertising.
Due
to the personal nature of mobile devices, pushing badly matched or unwanted
information onto users is undesirable. (Aalto et al.,
2002)(Kassinen,
2003) Aalto et al identified the importance of
directly “targeting the advertisements, so the user is not drowned in adverts” (Aalto
et al., 2002) and Kassinen indicates that most users
don't mind being pushed information, as long as they really need it. Although, this is a somewhat vague notion, as
what factors determine whether a user really needs a specific piece of
information?
Aalto
et al identified that the AD Server itself “has limited profiling
capabilities”, and that there is a perceived need for profiling, so that “the
user is not drowned in adverts”. This
highlights the necessity for a more adaptive approach to more closely matching consumers
with products.
Personalisation
Aalto
et al identified that there is a need for personalisation of content,
whilst talking about pushing advertisements to mobile devices. We extend this idea to embrace the concept
of using contextual data obtained from a mobile device and using this to
produce a completely personalised match.
Effective personalisation would allow us to market products directly at
an individual, as opposed to targeting a demographic.
We can look at personalisation as both the
desire to more closely match customer details against product details and the
ability to allow users to determine their preferences, i.e. we would like more
of this type of product or no more of this type of product. An ideal situation would be to present a
solution that provides a combination of these approaches, using contextual data
to make an intuitive and learned best guess, whilst allowing users to indicate
their feelings about the match and adapting accordingly. Lee et al introduced a system that learns
user preferences through a user agent, and then uses a matching agent to
closely match users to available services/events. (Lee et al., 2004)
In
order to personalise services, we need to assume that device users rarely
change, a point raised by Hofer et al.
(Hofer et al., 2003) A scenario with regular changing users would
drastically reduce the effectiveness of any personalisation.
Efficient
Matching
Context-aware
systems are by their very nature adaptive and because we cannot guarantee continuity
of service (Tandler, 2001), as users are permanently
moving in and out of service areas, this places considerable time constraints
on the services provided by the system.
Aalto et al identified that on average it took 37 seconds (for
positioning and push latency) to push an advert to a mobile device using
Bluetooth. (Aalto et al, 2002)
As to whether this overhead was due to inefficiencies in the position
mechanism or limitations in Bluetooth™ itself was not apparent,
yet the implications clearly indicate that for mobile advertising systems to be
viable, this overhead would need to be significantly reduced. However, with future developments it is
likely that this time will significantly decrease, but it highlights that the
decision process itself needs to be kept to an absolute minimum. The challenge here lies in producing high
quality matches, which users will perceive as required or suitable, in a small
amount of time.
Traditional matching algorithms are not wholly suitable to context-aware systems because contextual data is not always tractable, certain or easily matchable.
Unsolicited Advertising
Varshney et al suggested that mobile advertising is going
to be a very important class of mobile commerce (Varshney et al 2002),
but because of the personal nature of mobile devices there is broad scope for
abuse. Using local connection
technologies like Bluetooth or WLAN would provide a cost-free mechanism for
pushing advertisements to end-users, this raises the issue of dealing with
unsolicited advertisements or unwanted services, much like spam with
e-mail. Mobile phone spam, in the form
of unsolicited txt messages, has already reached epidemic proportions with 8
out of 10 mobile phones users reporting unsolicited messages (Jaques,
2005).
The key question here is how do we prevent unsolicited
advertisements or unwanted services without interfering with legitimate ones or
indirectly restricting the natural data flow of mobile context-aware
systems.
The B-MAD system (Aalto et al., 2002) side steps the issue by stating that its framework
focuses solely on permission-based advertising, therefore ruling out
unsolicited advertising (i.e. spamming).
Sadly, no mechanism for supporting such a permission based system was
presented. Alternatively, it would be
possible to consider other approaches derived from conventional spam prevention
techniques, such as Bayesian filtering or service blocking techniques. A more likely possibility is to use contextual
data to filter or restrict pushed advertisements based upon personal
preferences and end-user habits. For
example, we could define rules to only accept pushed adverts from shops that
the end-user has purchased items from in the last year.
Privacy
Context can contain data that is sensitive, such as
a user’s current location or current activity, so it is important to include
some mechanisms for privacy. A view
supported by Kourouthanasis et al says that “as
context-aware system offer increased personalisation, privacy concerns for the
capture and processing of context information is required.” (Kourouthanasis et
al., 2002) Hong & Landay, go as far
as saying that privacy is the most often-cited criticism of ubiquitous
computing, and may be the greatest barrier to its long term success. (Hong
& Landay, 2004) This point may seem
alarmist, but end users ultimately reject applications they
are uncomfortable using or find intrusive. (Hong & Landay, 2004) Because of the sharing nature of ubiquitous systems,
we need to ensure that privacy and security concerns are balanced against the
sharing nature or ubiquitous systems. Much
previous work on privacy tended to focus on providing anonymity or on keeping
personal information secret from hackers or unwanted sources.” (Hong,
2004) Therefore, it is essential that
privacy concerns are included at every stage of development of context-aware
applications, and “not done in an ad hoc manner or as an after thought.” (Hong
& Landay, 2004) This being is a major criticism of the B-MAD (Aalto et
al., 2002) system, which by admission has little or no consideration for
privacy.
Existing
systems for sharing contextual data such as Bluetooth™ and WLAN have previously
had security concerns, but because of the surge in popularity of these
technologies, emphasis has been placed on bolstering any security flaws,
resulting in effective secure solutions.
A number of existing context-aware
frameworks incorporate facilities for privacy, the Context Toolkit ()
introduces the concept of context ownership and CoBrA (Chen, 2004) has its own
specific privacy policy language called Rei (Kagal et al., 2003). Alternatively, Confab (Hong & Landay,
2004) is an infrastructure aimed at simplifying the task of creating
privacy-sensitive context-aware applications; it does this by addressing five
important common features that need to be supported.
- It identified three
basic interaction patterns for privacy-sensitive applications, these
being:
- Optimistic - applications
share personal information and detect abuses
- Pessimistic - where
more emphasis is placed on detecting abuses.
- Mixed-initiative - decisions to share information are made
by the end-user.
- Supports the tagging of personal information, that is marking
personal information with personal preferences, for example, a person’s
bank account may be available to certain secure institutions and not to
anyone else.
- Controls the access, flow and retention of personal
information, allowing us to include restrictions based on context types,
e.g. only allow co-workers to view my location between the hours of 9 to 5
pm.
- Control over precision of disclosed data, e.g. we could
disclose my address as either“16 Monks Road, Exeter” or “Devon”, depending
of the source of the request.
- Provides full logging facilities for both client and server,
providing the ability to fully monitor the flow and use of data in the
system.
Conclusion
Ubiquitous computing has enormous
potential for changing the way we think about computing, although the field is
still very much in its infancy. This is
due to a couple of reasons, firstly, creating ubiquitous environments was
expensive, most early work in ubiquitous computing originated from experimental
in-house systems where large companies could foot the bill for creating a
suitable environment. Secondly,
traditional developmental frameworks are not designed for ubiquitous
computing’s reliance on concurrency and parallelism; there was also a distinct
lack of any supporting infrastructure.
Although the sudden growth in popularity and availability of mobile
devices has presented ideal conditions for ubiquitous computing and the
emergence of projects like Indus presents a significant leap forward, the area
is still very much embryonic.
Ubiquitous computing though is here to stay
Context-aware applications offer a wealth
of potential, and it will not be long before we start seeing a significant
uptake in interest. When personal computers
where introduced in the early 80's they radically
altered our view of computing, giving rise to "desktop" computing,
technological and user expectations changed, old dominant companies who didn't
adapt quickly lost ground, new dominant companies appeared, computing
fundamentally changed. As Weiser
pointed out, “we still require much new work in operating systems, user interfaces, networks,
wireless, displays and many other related areas.” (Weiser, 1994) This signifies some idea of the size of
the challenge in hand. Ubiquitous
computing though is likely to be an altogether quieter revolution.
The majority of early work on ubiquitous
computing focused on context-aware applications, such as the Parctab and Active
Badge projects, where the focus was not on producing commercially viable
products. Whilst technically successful
these projects where greeted with scepticism by employees, some where concerned
over privacy, and others felt that the system was intrusive or that logged data
would be misused. Highlighting that one
of the biggest factors in a context-aware system is not necessarily the
technical challenge but getting the end-user to accept the system.
Context-aware systems have as yet been
limited to applications, which primarily use time or location as contextual
information and most examples are experimental and non-commercial
products. The success of GPS based
systems though has proved that context-aware applications can be commercially
viable products, although this success has only been possible because of the
US’s decision to freely allow access to GPS technology and resources. Context-aware systems are unlikely to become
widespread until adequate standardised methods of handling contextual data are
commonplace. An illustration of this
difficulty with handling contextual data being, how do we handle levels of
abstraction in context-based systems.
For example, take the simple question, “Where do I live?” This could provide numerous results, 16
Monks Road, Exeter, Devon, England, UK or Earth. Each of these answers is correct but usefulness depends on the
context of the question.
In terms of locating mobile devices the maturity of Bluetooth and WLAN
technologies has presented ideal cheap, secure, globally available, mechanisms
for local communication between devices.
Context-Aware applications for mobile
devices present probably the biggest commercial opportunity of any ubiquitous
systems, again technologies are in there infancy but it is unlikely that this
key market will be ignored for long.
Novel approach, like the B_MAD system (Aalto et al., 2002) have enormous potential but still have many hurdles (both
technical and personal) to overcome in order to produce successful viable
commercial solutions. As well as facing significant technical challenges,
application developers face having to place a larger emphasis on more human
factors. Marketing and advertisers are
likely to have already seen the potential that mobile devices offer, at present
advertisers focus their campaigns on particular demographics, but context-aware
applications would allow them to directly target individuals.
For mobile-based context-aware systems to
be accepted by the general public it is imperative that proper privacy and
security measures are deemed to be in place, consumer confidence is key.
End-users are already fearful of “big brother” scenarios, this was evident from
projects like Active Badge, where the majority of problems where not technical
but getting end-users to accept such systems. Products that seem intrusive or feel unsafe will be rejected;
ultimately it is users who will shape the future.
References
Aalto, L., Gothlin, N., Korhonen, J.,
Ojala, T., Bluetooth and WAP push based location-aware mobile advertising
system, MobiSys '04: In Proceedings
of the 2nd international conference on Mobile systems, applications, and
services, ACM Press, 2004, pp. 49-58.
Abowd., G. D., Dey, A., K., Wood, A.,
Applying Dynamic Integration as a Software Infrastructure for Context-Aware
Computing, ICSE, 1998
Abowd., G. D., Dey, A., K., Toward a
Better Understanding of Context and Context-Awareness, GVU Technical Report,
1999.
Abowd, G., Mynatt, E., Ubiquitous
Computing: Past, Present and Future, ACM Transactions on Computer-Human
Interaction, 2000, pp. 29-58
Abowd, G. D., Mynatt, E. D., Rodden, T.,
The Human Experience, Pervasive Computing, 2002, Vol. 1, pp. 48 -57.
Adult
mobile phone ownership or use: by age, 2001 and 2003: Social Trends 34, 2003,
National Statistics Online, viewed 14th December 2005,
<http://www.statistics.gov.uk/STATBASE/ssdataset.asp?vlnk=7202>
Baldauf, M., Dustar, S., Rosenberg, F., A
Survey of Context-Aware Systems, International Journal of Ad Hoc and
Ubiquitous Computing, 2005, forthcoming, <www.citeseer.ist.psu.edu/baldauf04survey.html>
Baudel, T., Beaudouin-Lafon, M., Charade:
Remote Control of Objects Using Free-hand gestures, Communications of ACM,
July 1993, Vol. 36, No 7, pp. 28-35
Bederson, B., Augmented Reality: A
prototype Automated Tour Guide, In Proceedings of ACM CHI’95, 1995, Vol.
2, pp. 210-211.
Borah, K., INDUS: A New Platform for
Ubiquitous Computing, viewed 29th November 2005, <http://www.acm.org/ubiquity/views/v6i36_borah.html>
Brown,
P., J., The Stick-e document: A framework for creating context-aware
applications, In Proceedings of the Electronic Publishing, Palo Alto,
1996, pp. 259-272.
Chen, H., An Intelligent Broker Architecture
for Pervasive Context-Aware Systems, 2004, PHD thesis, University of Maryland,
Baltimore County
Dey,
A., The Context Toolkit – a toolkit for context-aware applications, 2001,
viewed 2nd December 2005, <http://www.cc.gatech.edu/fce/contexttoolkit/>
Dey, A., Abowd, G., A Conceptual Framework and a Toolkit for Supporting the Rapid Prototyping of Context-Aware Applications, Human-Computer Interaction (HCI) Journal, 2001, Vol. 16, pp. 97-166.
Gelernter, D., Generative Communication in
Linda, ACM Computing Surveys, 1985, Vol. 7, no. 1, pp. 80-112.
Global Positioning Devices, Wikipedia,
viewed 15th November 2005, <http://en.wikipedia.org/wiki/Gps>.
Hofer, T., Schwinger, W., Pichler, M.,
Leonhartsberger, G., Altmann, J., Context-awareness on mobile devices – the
hydrogen approach, In Proceedings of the 36th Annual Hawaii
International Conference on System Sciences, 2002, pp. 292-302.
Hong, J., Landay, J., An Architecture for
Privacy-Sensitive Ubiquitous Computing, MobiSys '04: Proceedings of the 2nd
international conference on Mobile systems, applications, and Services, ACM
Press, 2004, pp. 177-189.
Indus platform Developer, Aumeganetworks,
2005, viewed 10 December 2005, <http://developer.aumeganetworks.com/>.
Jaques,
R., Spam plague hits 80 per cent of mobiles, www.computing.co.uk, 2005, viewed
29th December 2005, <http://www.computing.co.uk/vnunet/news/2126701/spam-plague-hits-80-per-cent-mobiles>
Java API, java.sun.com, viewed 17th
November 2005, <http://java.sun.com/j2se/1.4.2/docs/api/index.html>
Kagal, L., Finin, T., Joshi, A., A policy
language for a pervasive computing environment, In Proceedings of the 4th
IEEE International Workshop on Policies for Distributed Systems and Networks
(POLICY), 2004, pp. 63-74.
Kassinen, E., User needs for Location-Aware
Mobile Services, Personal and Ubiquitous Computing, 2003, Vol. 7, no.1, pp.
70-79.
Korkea-aho, M., Context-Aware Applications
Survey, Internetworking Seminar (Tik-110.551), Helsinki University of
Technology, 2000.
Kourouthanasis, P., Spinellis, D., Roussos, G., Giaglis, G., Intelligent cokes
and diapers: MyGrocer Ubiquitous Computing Environment, First International
Mobile Business Conference, July 2002, pp. 150-172.
Lee, G., Naganuma, T., Kurakake, S, Efficient Matching in a
Context-Aware Event Notification System for Mobile Users, Massachusetts
Institute of Technology, 2004, viewed 16 November 2005,
<http://people.csail.mit.edu/gjl/research/publications/lee05efficient.pdf>
Newman, W., Eldridge, M., Lamming, M.,
PEPYS: Generating Autobiographies by Automatic Tracking, ECSCW '91,
September 1991, pp. 175-188.
Picco, G. P., Balzarotte, D., Costa, P.,
LighTs: A Lightweight, Customizable Tuple Space Supporting Context-Aware
Applications, SAC, 2005, pp. 413-419.
Pascoe,
J., The Stick-e Note Architecture: extending the Interface Beyond the User, International
Conference on Intelligent User Interface, 1997, ACM. pp. 261-264.
Scilit,
B., Adams, N., Want, R., Context-Aware Computing Applications, IEEE Workshop
on Mobile Computing Systems and Applications, 1994, pp. 88-90.
Tandler,
P., Software Infrastructure for Ubiquitous Computing Environments: Supporting
Synchronous Collaboration with Heterogeneous Devices, In Proceedings of
UBICOMP2001, 2001, pp. 96-115.
Troung,
K., Abowd, G., Botherton, J., Who, What, When, Where, How: Design Issues of
Capture & Access Applications, In the Proceedings of UBICOMP 2001, 2001, pp.
209-224.
Varshney,
U., Vetter, R., Mobile Commerce: Framework, Applications and Networking
Support, Mobile Networks and Applications, 2002, Vol. 7, no. 3, pp.
185-198.
Want,
R., Hopper, A., Falcao, V., Gibbons, J., The Active Badge Location System, ACM
Transactions on Information Systems, 1992, Vol. 10, No 1, pp 91 – 102.
Want,
R, Schilit, B., Adams, N., Gold, R., Petersen, K., Goldberg, D., Ellis, J.,
Weiser, M., The PARCTAB Ubiquitous Computing Experiment, IEEE Personal
Communications, 1995, Vol. 2, no. 6, pp. 28-33.
Weiser,
M., The Computer for the 21st Century, Scientific American,
1991, pp. 94-10.
Weiser,
M., Some Computer Science Problems in Ubiquitous Computing, Communications
of the ACM, July 1993, pp. 137-143.
Weiser,
M., The World Is Not a Desktop, ACM Interactions, Jan 1994, Vol. 1, no.
1, pp. 7 – 8.
Weiser,
M., Ubiquitous Computing, 1996, Xerox, viewed 3rd December 2005, <http://www.ubiq.com/hypertext/weiser/UbiHome.html>